Phishing Revisited

Phishing Revisited
Let’s Revisit “Phishing,” Shall We?
We want you to be very aware.
DEFINITION: Phishing is a criminal act (generally under ‘wire fraud’) of gathering confidential information with the malicious intent of stealing from others. An article we published at the end of 2020 was about trying to scam people into paying for photo rights.
Phishing usually starts as an email with a veiled threat that immediate action must be taken or some dire consequence may occur. It seems legitimate and often comes from a brand you use or trust. An example may be: “Your domain name is about to expire and already has a buyer ready to purchase. Renew immediately to keep from losing your domain name!” Then a link to log into your account. At which point you are logging into a server that is logging your username and password (and maybe more).
Being in business for nearly 15 years (and personally being in the online industry for nearly 25 years), we’ve seen a lot of SPAM, malicious emails, and scams in particular. Browsers and email programs do very well in giving warnings, but we have a few things we watch for. Here are some steps to take BEFORE clicking any link.
- Short messages from trusted friends or businesses with a link that says something like “Check this out!” Or “Is this what you were talking about?” Regardless, it could be even a Google link that is often used for sharing files. DON’T IMMEDIATELY CLICK IT! It could be malware or a phishing scam.
- Before Clicking ANYTHING, verify the sender. This is also not quite enough. Scammers know how to ‘spoof’ or duplicate a sender’s email. Especially from someone that has already been scammed or hacked.
- HOVER over links. This helps. Usually, the link should include the company’s domain name. In the case of email companies like MailChimp and Constant Contact, the links should still go to the company’s website. So a link to ‘log into your account’ should include the domain name. BUT BE WARY! Some clever scammers will create ‘subdomains’ to fool you. Like, “https://bluezoocreative.7wzqueue.com” to fool you. The domain name you’re logging into is actually at “7wzqueue.com”!
- Be SAFE and go directly to the site in question. Skip the link in the email completely. Go RIGHT to the site referenced and log into your account ensuring you’re in the right place and double-check the issue in question.
- CALL or CHAT. Once logged in, if you don’t see any mention of the issue, hop on a chat or call the company to confirm for peace of mind.
“But, guys!
Who has time to check
all the emails like that?”
Better to spend a few minutes now than accidentally lose your identity, money, or more. Ask anyone who has had to deal with situations like this. A few minutes is nothing compared to having your site hijacked, bank accounts emptied, services locked out, social media channels inaccessible, and having to reissue bank and credit cards (and checks too).
NOT EVERYTHING IS PHISHING
Some things are just bad design and planning. Let me give you an example of something that happened to Blue Zoo (without naming names, of course.)
- Email Notification with a threat. This message came in from a trusted vendor. The threat was offset by the chance for free service. I checked the email sender and it seemed legit. But something felt ‘off.’
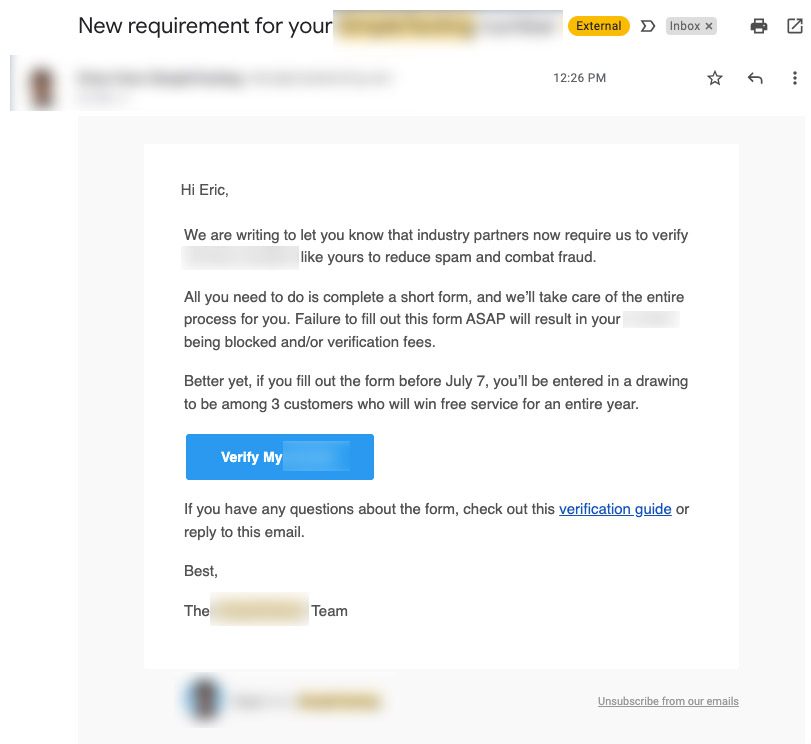
- Link seemed malicious on the big blue button. It had the company name in it, but as mentioned before, it was part of a subdomain name. So the link was even stranger, like: company-7qrx555681382.other-company-name.com. This was followed by a long string that we recognize as a tracking code. But what was it tracking? Regardless, I clicked the link.
- New domain name + immediate request for business information. The link to me to a new domain name that was tied to a form capture online software with an obscure subdomain name, like “wm-tq-788d.superform.com”. It immediately said, “You’ll need your business EIN and screenshots of…”
- Logged into my actual business account. At that point, I backed up and went to the business account to a linked article. There was no specific information I needed. So I logged into my account and hopped on a chat conversation. After making it past the BOT to a real person, and asking several times to verify the very phishy link in the email, the staff member verified the link was legit. I did take a few minutes to explain that their email and form links were very suspicious.
Total TIme Lost?
Maybe 15-20 Minutes
(not counting writing this article)
If you are going to get clients or potential customers to fill out any information, reset passwords, join an event, and otherwise ask people to share confidential information, make sure it is communicated if you are using a third-party platform. The other platform MAY actually be more secure than your own website. We actually don’t recommend storing that kind of information on your own website but can help you make for a better customer experience.
Blue Zoo will never send you obscure links to click! So, the next time you get an email telling you to update anything, take a beat. Then, check the sender, look over the link URL, and then verify the authenticity by going to your own account instead of the link provided. If all else fails, reach out to the service and hop on a chat. Peace of mind is worth a lot.


